Cross-Chain Swap Risks 2026: A Trader’s Guide
What Cross-Chain Swaps Are (and Why Traders Depend on Them in 2026)
A cross-chain swap is a single workflow that exchanges an asset on one blockchain for an asset on another blockchain, typically by combining a bridge or messaging layer with one or more on-chain swaps and relayers/routers. For example, swapping USDT on Arbitrum into ETH on Base without manually.
In 2026, cross-chain activity is no longer “advanced user only.” Liquidity is fragmented across L1s, L2s, and app-chains, so traders routinely chain-hop to:
- rebalance capital where yields and liquidity are best,
- access new token launches and ecosystems,
- reduce costs by executing on lower-fee networks.
That convenience is exactly why cross-chain swap risks remain one of the biggest risk concentrations in Web3.

The Core Cross-Chain Swap Risks Traders Face in 2026
Cross-chain swap risks are layered because a single “swap” can touch multiple chains, multiple smart contracts, and multiple operational systems. Below is a trader-friendly risk taxonomy you can use to sanity-check any route.
| Risk category | What can go wrong | What it looks like for traders |
|---|---|---|
| Protocol and architecture | Bridge logic bugs, weak message verification, over-centralized multisigs/validators, wrapped-asset backing breaks | A wrapped token becomes unbacked, funds stuck, or catastrophic loss after a bridge exploit |
| Economic and liquidity | Thin liquidity, compounded slippage across steps, liquidity fragmentation across wrapped variants, de-pegs | You receive materially less than quoted, or you end up holding a discounted wrapped asset |
| Operational and infrastructure | Chain congestion, gas spikes, downtime, paused bridge contracts, relayer delays, reorg/finality issues | Swap takes far longer than expected, completes partially, or appears “stuck in transit” |
| Security and adversarial | Key compromise, verification bypass, exploit-driven laundering, malicious contracts | Funds drained, approvals abused later, or you unknowingly interact with high-risk endpoints |
| UX and human error | Wrong chain, wrong token standard, unlimited approvals, phishing bridge UIs | “I sent it but never got it,” or wallet gets drained after signing “one quick approval” |
| Regulatory and compliance | Sanctioned contract exposure, tainted routes, reporting complexity | Deposits to exchanges get flagged, or your cross-chain history becomes difficult to document |
Two practical implications matter most for retail and active traders:
- You are not just evaluating price. You are accepting an execution path with security, liquidity, and operational assumptions.
- Wallet design is part of risk management, because the wallet is where you see route details, approvals, warnings, and final outcomes.
For deeper technical background on bridge vulnerability patterns, see:
- https://chain.link/education-hub/cross-chain-bridge-vulnerabilities
- https://www.certik.com/resources/blog/cross-chain-vulnerabilities-and-bridge-exploits-in-2022
What History Teaches: Why Bridge Failures Keep Hitting Users
Bridge and interoperability exploits have repeatedly produced losses in the hundreds of millions. CertiK reported that in 2022, bridge attacks represented a major share of Web3 losses, totaling roughly $1.3B across five major incidents (one commonly cited estimate Source)
The recurring patterns are consistent
- Centralized control (small multisigs/validator sets) gets compromised.
- Verification logic breaks (attackers forge proofs or bypass checks).
- Wrapped assets inherit bridge risk even if you never used the original bridge UI.
Here is a quick reference of several major incidents and their approximate losses
- https://www.startupdefense.io/cyberattacks/cross-chain-bridge-exploit
- https://www.gate.com/learn/articles/the-top-10-biggest-crypto-hacks-in-history/7467
| Incident | Approx. loss | Cause |
|---|---|---|
| Poly Network (2021) | ~$610M | Smart contract vulnerability enabling unauthorized transfers |
| Wormhole (2022) | ~$320M | Verification bypass leading to unbacked minting |
| Ronin (2022) | ~$620M | Validator key compromise in a small validator set |
| Nomad (2022) | ~$190M | Logic bug enabling repeated draining transactions |
| Harmony Horizon (2022) | ~$100M | Multisig key compromise |
| Orbit Bridge (2024) | $80M+ reported | Multisig compromise (reported) |
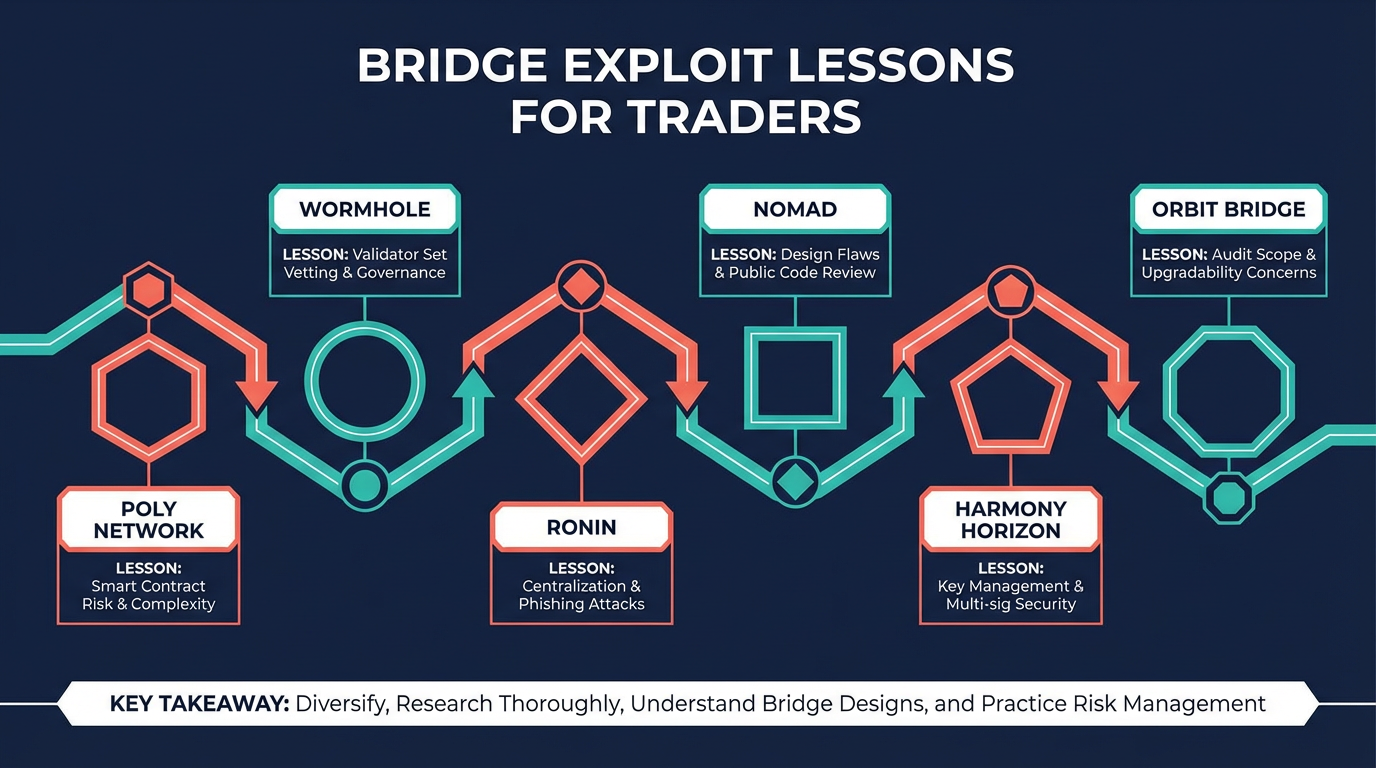
Takeaway for traders: the biggest failures are not “price moved against me,” but “the route’s trust assumptions failed.” That is why wallet-level guardrails (warnings, contract recognition, phishing protection, and clear route disclosure) matter.
Tutorial: A Safer Cross-Chain Swap Workflow in FoxWallet (Wallet-Level Risk Controls)
FoxWallet is a multi-chain decentralized wallet (non-custodial). Your keys remain under your control, stored locally with encryption and secure isolation. For cross-chain swaps, FoxWallet integrates multi-chain swap aggregators natively and focuses on pre-transaction risk alerts, smart contract recognition, and phishing protection.
Use this step-by-step workflow to reduce cross-chain swap risks before you sign anything.
Step 1: Confirm the “from” and “to” chains and assets
- Double-check the source chain and destination chain.
- Verify the token symbol and (when shown) the contract identity.
Why it matters: wrong-chain mistakes are one of the fastest ways to create “missing funds” scenarios, especially when bridged assets exist in multiple wrapped forms.
Step 2: Read the route details like a trader, not a tourist
When FoxWallet returns a quote via an integrated aggregator, focus on:
- Total fee breakdown (network fees plus protocol fees).
- Expected slippage and whether it is compounded across multiple steps.
- Estimated completion time (some designs are intentionally delayed).
If the route looks unusually complex for a simple transfer, consider reducing size or choosing a different asset pair with deeper liquidity.
Step 3: Treat approvals as a separate security decision
Before the swap transaction, you may be asked for a token approval (allowance). Best practice:
- Avoid unlimited approvals when a limited approval is feasible.
- Re-check the contract being approved and the action being requested.
Why it matters: many real-world wallet drains start with a single careless approval, then the attacker pulls funds later.
Step 4: Use FoxWallet’s pre-transaction warnings as a stop sign, not a suggestion
FoxWallet’s security stack is designed to surface risk before signing:
- smart contract recognition,
- pre-transaction risk alerts,
- phishing and malicious link protection.
If an alert triggers, pause. The fastest “recovery” is not signing the transaction.
Step 5: Verify receipt on the destination chain and update your portfolio view
After execution:
- Confirm you received the correct asset on the destination chain.
- If you received a wrapped variant, recognize that it can carry bridge-related de-peg risk.
FoxWallet’s unified multi-chain asset view and real-time on-chain synchronization help reduce the “I can’t find my funds” problem by showing assets across networks in one place.
2026 Compliance Reality and a Practical Checklist (Before You Swap)
Cross-chain services are frequently referenced in compliance discussions because chain-hopping is a common laundering technique. Elliptic reported at least $3.6B in illicit and high-risk funds routed via cross-chain services (as cited in its cross-chain crime reporting):
Regulatory pressure is also trending toward contract-level scrutiny (including sanctioned smart contract addresses) and heavier “know-your-transaction” expectations:
- https://www.globallegalinsights.com/practice-areas/blockchain-cryptocurrency-laws-and-regulations/usa/
- https://kyc-chain.com/kyt-know-your-transaction-crypto-compliance-2026/
Quick checklist you can reuse
- Validate chains and token type (native vs wrapped).
- Prefer routes with clear fees, reasonable slippage, and realistic timing.
- Minimize approvals and never sign what you do not understand.
- Watch for wallet warnings about suspicious contracts or phishing.
- After completion, confirm receipt on the destination chain and label any wrapped assets in your own tracking.
If you want a wallet experience built around multi-chain visibility, non-custodial control, and proactive risk warnings for cross-chain activity, use FoxWallet on mobile or the browser extension and make the checklist above your default workflow.
Extra overviews of how swapping routes are composed may also be found by the following links:
